10 Security Tips for Average Users¶
Last Update: Jan 09, 2022

Recently I was tasked to produce a document outlining 10 key points that would empower users to make better security choices thus increasing their overall security posture.
Microsoft and Google both have interesting information that served as inspiration for this document and while I certainly wouldn’t compare this documentation to that of Google or Microsoft, hopefully this will be of use to someone.
So without further ado, here are 10 security tips for the average user:
1. Technology is your last line of defense¶
Many users are of the opinion that technology is a panacea and while it’s true that in many cases technology will do it’s utmost to keep you safe and secure, it should be seen as your last line of defense.
Remember that technology is fallible; it can put you at risk just as easily as protecting you from risk.
Rather, security should be seen as the responsibility of every user and as such it is up to you to ensure that you make sensible decisions when interacting with your computing device of choice.
2. Be vigilant. Be suspicious¶
It’s a good idea to treat everything with a healthy dose of suspicion, and there are a few good reasons for this:
The FROM address of an e-mail is easily faked;
Phishing sites can be made to appear identical to the sites you trust;
If an offer is being made that sounds to good to be true, it probably is;
3. Verify, Verify, Verify¶
If you are doing step two correctly, there will be times when you won’t be 100% certain about the authenticity of something.
Let’s look at specific cases and how you should address them.
You receive an e-mail from a trusted friend with a strange attachment? Should you run it?
The short answer is no. These sorts of messages are usually the result of a spoofed e-mail, or sometimes as a result of your friend’s e-mail account having already been compromised by an attacker. If you want 100% certainty, pick up the phone, and verify if it was indeed them that sent it to you.
You receive an e-mail from what appears to be your financial provider or IT organization asking you to log in with your credentials. Should you click on the link and input your credentials?
Your suspicious nature should serve you well here. These types of e-mails are almost always [Phishing] [3] mails, designed to steal your sensitive information. The first thing you should do, is hover over the link you’re wanting to click on. Doing this will cause your e-mail client to display the actual link it will be sending you to. If the two don’t match, as seen in the screenshot below, then you shouldn’t even click on the link at all.
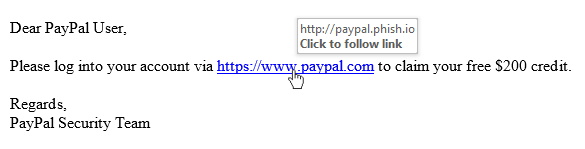
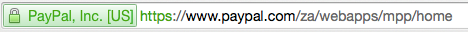
Assuming that the two match and you feel safe enough to click on the link, you should now verify that the site is using SSL (ie, it is secure) by ensuring your browser verifies this. An example of this in Chrome can be seen below:
In Safari, it should look something like:

In FireFox, this will look like:

As you can see, both Chrome and Safari give a visual indicator with a color coded reference to how safe the browser believes you are. More information on the SSL lock in Google Chrome can be found [here] [4].
In summary, if the lock isn’t there, or it isn’t green, you shouldn’t trust the site and you certainly shouldn’t be inputting your credentials.
4. Stay up-to-date¶
New security vulnerabilities are found daily. As such it’s important to ensure that you keep the software on your machine up-to-date at all times. This includes, but is not limited to:
Operating System Updates
iOS Updates
Android Updates (if your vendor provides them)
Java Updates
Flash Updates
Anti-Virus Updates
Most users corporate IT divisions will do this for them, but if you have your own device it’s important to remember these principles.
5. Use Strong, Unique Passwords¶
Weak passwords put you at risk. Using a single weak password for all your different accounts and services is just a bad idea. It means if your password is compromised in one place it’s compromised everywhere.
There are a few simple rules when it comes to passwords:
They should be strong; strong passwords by today’s standards should be 12 characters or above with a mixture of alphanumeric and special characters.
They should be unique; you should use a password once and only once.
They shouldn’t be written down on post-it notes left around for other people to discover.
The problem with these rules are two-fold:
Coming up with strong passwords is difficult when done manually.
Remembering those passwords without post-it notes is nigh on impossible.
Don’t be afraid to use tools to help you with this. 1Password and LastPass are both excellent password managers that can help you achieve password nirvana by generating and storing your passwords securely.
The caveat to using these tools is that they rely on you having an extremely strong master password to protect all the other passwords, so be sure to come up with something really strong here, typically 20+ characters… a passphrase is usually a good idea and easier to remember.
6. Use Two-Factor Authentication¶
Some of the applications and services that you use on a daily basis are more important to you than others. This list would be different for everyone, but for most people it probably includes services like:
Dropbox
Gmail
Twitter
Facebook
These services typically host data or content that you feel is potentially sensitive or where someone posing as you could do damage to you from a credibility perspective.
For these services, two-factor authentication is recommended as an added security measure. In essence, 2FA means you need to enter something you know (your password), as well as something you have (an OTP from your smartphone typically) to prove that you are who you claim to be.
7. Protect yourself on open wi-fi networks¶
If you paid attention to number two in this list, you should already be suspicious of open wi-fi networks in general. While open wi-fi networks are not always malicious they offer attackers an opportunity to potentially snoop on unsuspecting victims. There are some basic steps that you should take to ensure your safety if you choose to use these networks.
This includes, but is not limited to:
Using VPN when on an open wi-fi network to ensure all your traffic is sent over a secure channel;
When browsing, ensure that you connect only via HTTPS and that the certificate is verified as described in section 3. Verify, Verify, Verify.
8. Be wary of pirated software¶
Ethical issues aside, pirated software and key generators etc. offer an easy way for attackers to infect your device with malware and other unwanted software. The simple solution is just don’t do it.
9. Secure Your Data¶
Securing your data is somewhat more complex than it sounds. There are a number of ways that your data could be exposed, but here are a few simple ways to help protect your data:
Ensure that you have backups of your critical data;
Lock your computing device when you’re stepping away from it;
Set up your computing device to require a password on wake;
Encrypt your sensitive data where required.
10. Don’t be afraid to ask for help¶
Most of us have access to someone who is knowledgeable in the IT space, or have IT departments at work with dedicated security functions. Don’t be afraid to ask if you have questions or doubts about something. Nobody knows everything, and there is no shame in asking. The old adage ‘Rather safe than sorry’ comes to mind.